BitLocker is a built-in encryption feature in Windows that helps protect data by encrypting entire volumes. Managing and automating BitLocker can greatly simplify encryption tasks, especially in larger environments.
This article will answer your questions by exploring the common PowerShell commands and providing guidance on automating BitLocker deployment.
Using PowerShell to Manage BitLocker
PowerShell offers a variety of commands for managing BitLocker, enabling administrators to handle encryption tasks efficiently.
1. Enabling BitLocker
To enable BitLocker on a drive, use the Enable-BitLocker command. This command initializes BitLocker encryption on the specified volume.
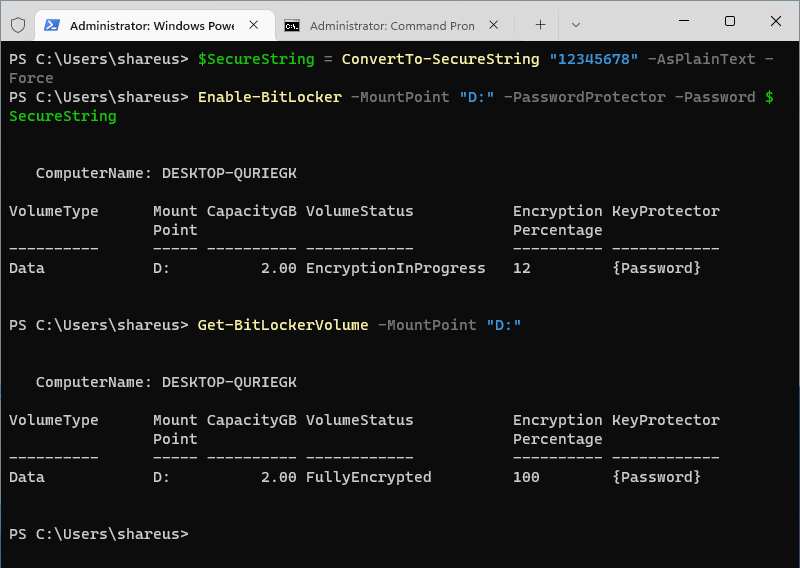
$SecureString = ConvertTo-SecureString "12345678" -AsPlainText -Force
Enable-BitLocker -MountPoint "D:" -PasswordProtector -Password $SecureString
This command enables BitLocker on the D: drive with a specified password as the protector(12345678).
Caution: By default, passwords must be at least 8 characters in length. If you want to modify it, you can refer set BitLocker minimum password length.
2. Getting BitLocker Status
To check the BitLocker status of a volume, use the Get-BitLockerVolume command. This is helpful for verifying the encryption status of drives.
Get-BitLockerVolume -MountPoint "D:"
This command displays the BitLocker status for the D: drive.
3. Enabling BitLocker Auto Unlock
For convenience, you can enable BitLocker to automatically unlock a drive on system startup using the Enable-BitLockerAutoUnlock command.
Enable-BitLockerAutoUnlock -MountPoint "D:"
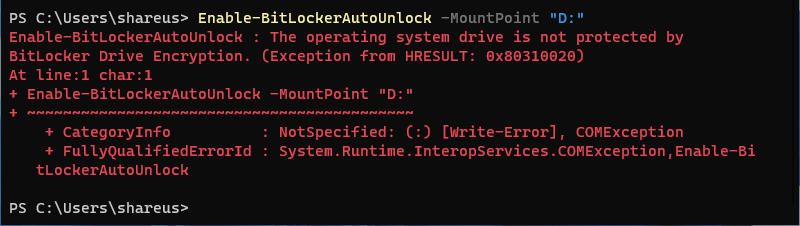
This command enables automatic unlocking for the D: drive.
Note: Before enabling this feature, you must encrypt the operating system drive with BitLocker.
4. Suspending BitLocker Protection
In some cases, you may need to temporarily suspend BitLocker protection, such as during system maintenance or updates. Use the Suspend-BitLocker command.
Suspend-BitLocker -MountPoint "C:" -RebootCount 0
This command suspends BitLocker protection on the C: drive until manually resumed.
Note: This command is specified for the operating system drive.
5. Resuming BitLocker Protection
To resume BitLocker protection after it has been suspended, use the Resume-BitLocker command.
Resume-BitLocker -MountPoint "C:"
This command resumes BitLocker protection on the C: drive.
6. Disabling BitLocker Protection
If you need to disable BitLocker protection, use the Disable-BitLocker command. Note that you may need to clear auto-unlock keys first.
Disable-BitLocker -MountPoint "D:"
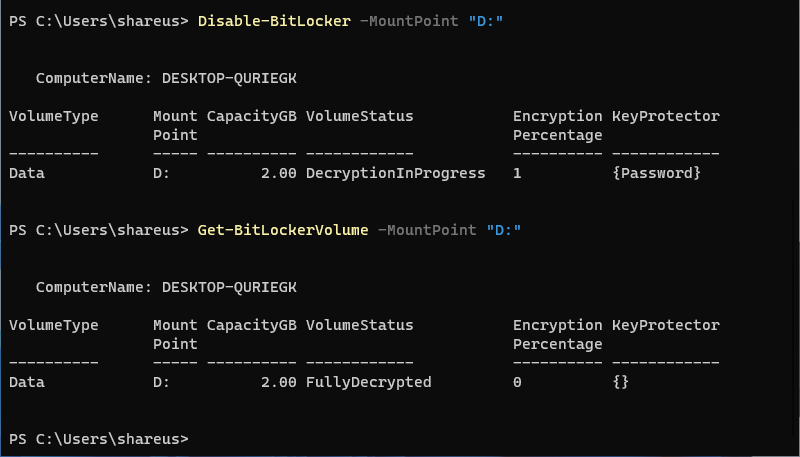
If this command encounters issues, clear the auto-unlock keys and try again:
Clear-BitLockerAutoUnlock
Disable-BitLocker -MountPoint "C:"
This ensures that all auto-unlock keys are removed before disabling BitLocker.
For more commands, refer to the official PowerShell BitLocker module documentation.
Automating BitLocker Deployment with PowerShell
Automating BitLocker deployment can save time and ensure consistency across multiple systems. You can use comprehensive scripts to manage BitLocker settings and automate encryption tasks.
One useful script is provided by Stephane van Gulick. This script can be customized to fit various deployment scenarios and streamline BitLocker management.
For more information, refer to the PowerShell BitLocker Encryption Tool: Swiss Army Knife.
Summary
Managing and automating BitLocker with PowerShell significantly simplifies the process of encrypting and protecting data on Windows systems. By leveraging PowerShell commands and scripts, administrators can efficiently handle BitLocker tasks, ensuring data security across the organization. For detailed script explanations and further automation ideas, explore the Microsoft Scripting Blog on PowerShell and BitLocker.




